Series
Proven Practices for Managing App Registrations in Entra ID
1: What Are App Registrations in Microsoft Entra ID?
2: Assigning App Ownership and Avoiding Shared Registrations in Microsoft Entra ID
3: Credential and Permission Management for App Registrations in Entra ID (you are reading this article)
4: Controlling App Registration Growth in Microsoft Entra ID
Once your apps have clearly defined owners and responsibilities (see Part 2), the next layer of protection is managing how they authenticate and what they can access.
This is where problems often build up quietly. Credentials are reused or forgotten. Apps accumulate permissions far beyond what they need. And without guardrails, anyone can create new registrations that slip past IT.
In this article, we’ll walk through three practices that help keep your app identity landscape under control:
- Managing credentials securely and avoiding expiry surprises
- Applying the principle of least privilege to app permissions
- Restricting app registration rights to avoid shadow IT
Each one addresses a common blind spot in Microsoft Entra ID. And each one lays the groundwork for a more secure, manageable, and predictable identity environment.
Best Practice 4: Choose the Right Credential Type for Each App
To authenticate securely in Microsoft Entra ID, an application needs a credential. This credential proves the app’s identity and allows it to request access tokens for services like Microsoft Graph, SharePoint, or custom APIs.
Credentials can be executed in two ways:
- Delegated Permissions (User + App Context) – allow an application to act on behalf of a signed-in user. The effective access is determined by the union of the user’s permissions and the application’s permissions, meaning the app can only perform actions that are permitted for both.
- Application Permissions (App-Only Context) – allow an application to authenticate and operate independently of any user. In this mode, the app runs with its own identity and can access resources directly, without requiring user sign-in or consent at runtime.
Depending on the setup, the app uses either a client secret or a certificate, which work like a password for the application and request authentication tokens.
Microsoft Entra ID supports two primary types of credentials for app registrations:
- Client secrets (similar to passwords)
- Certificates (cryptographic keys)
For those new to this topic, it helps to think of these credentials like keys that the application uses to unlock secure communication with Microsoft services. Just as you wouldn’t want to share the same house key with too many people or leave it in an insecure place, application credentials must be managed carefully to avoid misuse.
Microsoft recommends using certificates instead of client secrets whenever possible. Certificates offer stronger protection because they are harder to guess or extract, and they integrate well with secure storage systems.
Best Practice 5: Handle Short Lifespans for credentials and use Secure Storage
- No matter which type of key you are using you should always try to have a short time span of validity for such keys: set short expiration periods (ideally 6 months or less)
- Avoid storing secrets in plain text in scripts, files, or shared documentation
- Use Azure Key Vault to store secrets and certificates securely
Shorter lifespans limit your exposure if a secret/credential is ever leaked, and secure storage keeps sensitive information out of reach from unauthorized users.
Best Practice 6: Monitor Credential Expiry to Prevent Outages
Since we are reducing the time span of a credential, we are also increasing the risk of service disruptions when such credential is expiring and no longer usable and our application hasn't received a new credential to authenticate. If a secret or certificate expires and isn’t renewed, the app will lose access and may stop functioning, potentially causing service outages.
To prevent this:
- Monitor expiration dates using Microsoft Graph API
- Track which apps have credentials nearing expiry and act before their service is disrupted
A proactive approach avoids last-minute scrambles and unplanned outages.
Best Practice 7: Review Credentials Regularly to Clean Up Old Access
Over time, apps may be deprecated, replaced, or forgotten, yet their credentials often stay behind.
Regular credential reviews help you:
- Remove stale or unused credentials
- Limit the risk of forgotten access falling into the wrong hands
- Reduce your exposure across the identity environment
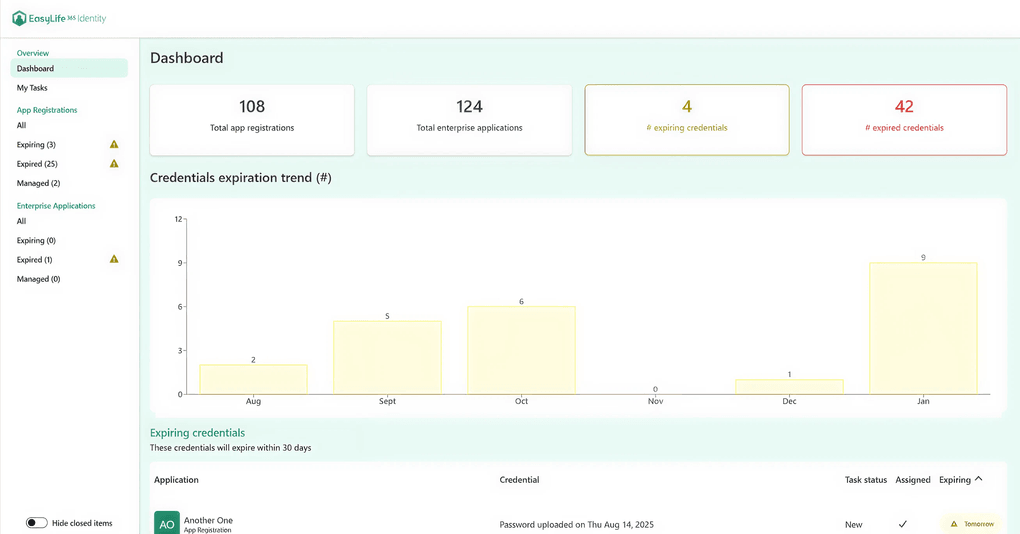
To streamline this process, EasyLife 365 Identity offers enhanced credential governance features. It provides centralized visibility into all registered applications, highlights credentials that are expiring or outdated, and enables automatic or semi-automated renewal workflows.
|
|---|
| Expiring credentials overview in EasyLife 365 Identity dashboard. |
These capabilities are integrated with the application ownership and sponsorship models introduced in Part 2 of this series, so the right people, those responsible for the application, are notified when action is needed. This ensures that credential management is not happening in isolation but as part of a broader, accountable governance process.
Proper credential management is not just a technical concern, but it is a fundamental security practice. When credentials are treated with the same care as user passwords or access keys, you reduce the risk of both accidental outages and malicious access.
Best Practice 8: Apply the Principle of Least Privilege to App Permissions
When an application is registered in Microsoft Entra ID, it often needs permission to access Microsoft 365 services or APIs like Microsoft Graph. These permissions determine what the app is allowed to do on behalf of a user or the organization.
An app might request permission to read user profiles, send emails, access calendars, or even update directory settings. While many of these requests are legitimate and necessary, they can easily open the door to a broader security concern: over-permissioned apps.
This is where the principle of least privilege becomes essential. It is a fundamental concept in cybersecurity that states any identity, whether a user, device, or application, should have only the minimum level of access required to perform its function and nothing more. When this principle is not applied, applications are often granted far more power than they actually need.
For example:
Consider a reporting application that only needs to read user profile information. If it is granted the Directory.ReadWrite.All permission, it now has the ability to create, modify, or delete objects in your entire Entra ID tenant. If the app is ever compromised, this level of access gives an attacker the opportunity to manipulate critical parts of your directory, potentially leading to data loss, privilege escalation, or lateral movement across your environment.
Similarly, if a misconfigured app is granted access to users' email inboxes when it only needs calendar access, it becomes a much more attractive and dangerous target.
There are two types of API permissions in Microsoft Entra ID:
- Delegated permissions, which require a signed-in user and allow the app to act on the user's behalf, respecting their access rights
- Application permissions, which allow the app to act independently of a user, often with broader and more powerful access
Where possible, it is safer to use delegated permissions, as these are scoped to the specific user’s access level and application permissions. More precisely, it refers to the intersection between the permissions granted to a user and those granted to the app. Application permissions, on the other hand, should only be granted when absolutely necessary, and only to applications that are well protected, well monitored, and clearly owned. Note that this doesn’t mean you shouldn’t assign application permissions to an app. There are many cases where doing so is appropriate for your use case.
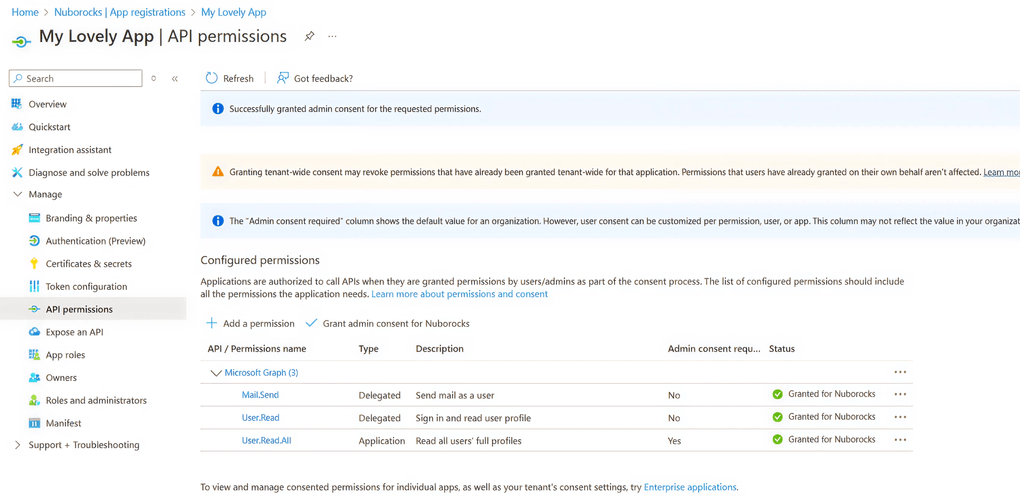
To manage these permissions, administrators can use the API permissions blade within the app registration settings in the Entra admin portal.
|
|---|
| Entra ID permissions screen with delegated and application API scopes. |
This interface shows:
- Which permissions an application has requested
- Whether admin consent has been granted
- What kind of data the app can access
Reviewing this list regularly helps ensure that apps are not quietly accumulating dangerous privileges over time.
Consent can be granted in two different ways:
- By an administrator – for organization-wide scenarios or when an app requires higher-privileged permissions that users cannot approve themselves.
- By individual users – in cases where the app only requests permissions that users are allowed to consent to on their own behalf. This often applies to delegated permissions with low impact, such as reading basic profile data.
It is also important to note that reviewing the list in the application blade alone is not sufficient. Administrators can freely add or remove entries there, but these changes do not directly impact what the application is actually allowed to do. The effective set of permissions is determined by the service principal that represents the application instance in your tenant.
In practice, this means that: The permissions shown in the app registration blade may differ from those granted on the service principal.
Only the permissions that were explicitly consented either by an administrator or by a user at the point of use are valid and enforced. If the service principal has retained older, broader permissions that are no longer visible in the app registration blade, the application may still operate with higher privileges than expected.
This distinction makes it critical to review not only the app registration, but also the service principal objects in your tenant. Overlooking this could result in shadow permissions, privileges that persist silently even after an app’s registration settings appear to have been tightened.
Regularly auditing service principals, comparing their effective permissions to those displayed in app registrations, and removing unused or misaligned privileges are essential steps in maintaining a least-privilege environment.
Best Practice 9: Use Admin Consent Workflows to Control Sensitive Access
For applications that request high-level or sensitive permissions, organizations should enable the Admin Consent Workflow. This feature provides a built-in approval process for apps requesting permissions that users are not allowed to grant on their own.
Rather than relying on users to understand the risk of a permission like Mail.ReadWrite, the workflow routes the request to an admin or security team. They can assess whether the access is justified before approving it. This helps prevent accidental over-permissioning caused by misunderstanding or social engineering.
Granting too many permissions to applications can significantly increase your organization’s attack surface. If just one app with excessive permissions is compromised, whether through leaked credentials, a vulnerability, or insider misuse, it can open the door to widespread damage.
That is why the principle of least privilege is so important. It limits the potential impact of any one app being misused. By applying this principle, organizations can greatly reduce their exposure to unauthorized access, data breaches, and identity misuse, while still enabling the apps their users and teams rely on.
Best Practice 10: Restrict Who Can Register Apps in the Tenant
In Microsoft Entra ID, any user in the tenant is allowed by default to create app registrations. While this default setting supports flexibility for developers and teams experimenting with applications, it also introduces significant security and governance risks, especially in larger or more regulated environments.
When users can freely register applications, they can also generate credentials and request API permissions that allow those apps to access Microsoft 365 data or interact with other cloud services. Without oversight, this leads to a phenomenon known as shadow IT —technology tools and integrations that operate outside of IT’s visibility and control.
Shadow IT introduces a number of risks:
- Applications may be configured incorrectly
- They may request excessive or unnecessary permissions
- Secrets might be stored insecurely
- Apps can be abandoned after testing, leaving unused credentials behind
To prevent this, Microsoft Entra ID includes a setting that allows administrators to restrict who can create app registrations.
This configuration is available under User Settings in the Entra admin center. From here, you can:
- Disable the default permission that allows all users to register apps
- Allow only selected members of an Entra ID security group to create and manage app registrations
This security group should include only trusted users who understand app registration best practices. This might include:
- Members of a DevSecOps or Cloud Platform Engineering team
- Approved developers in designated departments
By limiting this ability, you ensure that any new app registration is created by someone who understands how to configure it securely, assign appropriate permissions, manage credentials, and follow your organization’s governance policies.
In smaller organizations or development-heavy environments, it might be appropriate to allow broader access. But even in these cases, it is important to monitor app creation activity and ensure that users are aware of the risks and responsibilities involved in managing an application identity.
Restricting who can register apps also improves auditability and accountability. When only a known group of users can create app registrations, it becomes much easier to answer key questions:
- Who created this app?
- Why does it exist?
- Who is responsible for it?
This reduces the risk of apps being left unmanaged, misconfigured, or over-permissioned.
We built EasyLife 365 Identity to strengthen this control point because one of the earliest patterns we saw was clear:
Application chaos often starts when anyone can register an app without oversight.
Without defined boundaries, apps show up with:
- No owner
- No sponsor
- No business justification
EasyLife 365 Identity addresses this by allowing you to define who can create or sponsor applications at a fine-grained level and to track registration activity over time. With integrated lifecycle workflows, it also ensures that any newly created app has defined ownership, proper tagging, and an initial review process. These guardrails reduce the chances of unmanaged or high-risk applications slipping through unnoticed.
By limiting app registration rights to a select group of responsible users, organizations can:
- Reduce security risk
- Eliminate unnecessary complexity
- Maintain tighter control over how apps integrate with Microsoft 365
Conclusion: Bringing Control Back to Credentials, Permissions, and App Creation
Credential misuse, over-permissioned apps, and uncontrolled registrations don’t just create technical debt, they quietly erode trust in your identity governance model.
In this post, we explored three essential practices to strengthen that model:
- Secure credential handling
- Scoping permissions according to needs
- Controlling who can register applications
When implemented well, these controls reduce the risk of misconfigurations, overexposed data, and identity-related incidents.
EasyLife 365 Identity supports these efforts by giving you the tools to detect expiring credentials, identify permission sprawl, and enforce app ownership from day one. It helps turn best practices into repeatable processes, integrated with how your teams already work.
In Part 4, we’ll wrap up the series by focusing on cleanup and continuous improvement. You’ll learn how to review app registrations regularly, define registration boundaries with app roles, and maintain a healthy application directory over time.