Serie
Proven Practices for Managing App Registrations in Entra ID
App registrations tend to grow quietly. What starts as a handful of integrations can quickly balloon into dozens or even hundreds of apps scattered across your Microsoft Entra ID tenant. Without the right controls in place, growth brings risk: unknown publishers, hardcoded access models, stale credentials, and apps no one is reviewing anymore.
Once you’ve covered the basics such as ownership and environments, credentials, and permissions, it’s time to think about scale. How do you maintain trust when apps are used externally? How do you define access roles cleanly across departments? And how do you keep your app directory from turning into a black hole?
This final post in the app registrations series explores the best practices that help you scale with control:
- Publisher verification for external trust
- App roles for structured, flexible access control
- Periodic reviews to eliminate sprawl and reduce risk
Best practice 11: Build External Trust for Multi-Tenant and Third-Party Apps
When your organization develops and distributes applications for use outside your Microsoft Entra ID tenant, they may be used by customers, partners, or other third parties. It is important to ensure that these applications are seen as trustworthy by users and administrators in other organizations. One way to establish this trust is by registering your organization as a Verified Publisher in the Microsoft identity ecosystem.
In Microsoft Entra ID, when an external user signs in to your app or an admin in another tenant sees a consent screen, the publisher information appears in the prompt. If your app is not verified, users will see a warning that says the app’s unverified warning.

|
|---|
| Consent Screen with “Publisher Could Not Be Verified” Warning. |
Why is this important?
- Users and admins in other organizations must trust your app before granting access to data.
- Warnings about untrusted publishers can lead to confusion, mistrust, or outright rejection, especially in business-to-business (B2B) scenarios.
- Lack of trust can become a blocker to adoption, even for secure and well-designed apps.
By obtaining Verified Publisher status:
- Your applications will display your organization’s verified name and domain on the Microsoft sign-in and consent screens.
- This removes the warning and gives users and administrators in other tenants greater confidence that the app is safe and originates from a known, validated organization.
Best Practice 12: Become a Verified Publisher in Microsoft Entra ID
The process to become a Verified Publisher is straightforward but requires a few steps.
Step 1: Verify Your Primary Domain First, you must ensure that your organization’s primary domain is verified in Microsoft Entra ID. This confirms that you own the domain and are eligible to represent it.
Step 2: Associate an App Registration Next, you must publish at least one app registration and associate it with your verified domain.
Step 3: Apply Through Microsoft Partner Center Finally, you can apply for publisher verification through the Microsoft Partner Center, where Microsoft reviews your submission and, once approved, marks your apps as verified across all tenants.
When is Verification Essential? This process is especially important if you are:
- Offering a multi-tenant SaaS product
- Developing line-of-business apps that will be deployed to customer environments
- Building integrations that require users or administrators in other organizations to grant consent to your app
Without verified publisher status, you may encounter resistance or delays during deployment. Admins may need to review and approve your app manually through conditional access policies or require additional documentation before allowing the app into their environment.
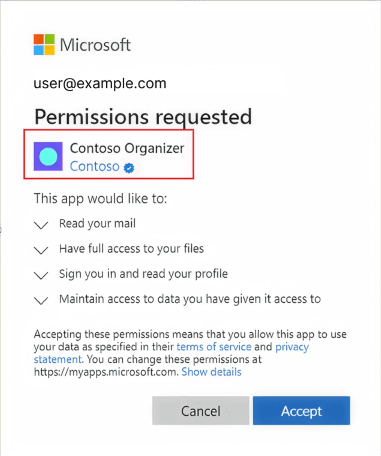
|
|---|
| Consent Screen for an app that has achieved Verified Publisher status. |
Verified publisher status is not just about branding. It is about transparency, security, and user experience. It communicates to other organizations that Microsoft has verified your identity and that your application is safe to interact with sensitive data and services.
Best Practice 13: Plan and Define Application Access Levels
When building or integrating applications with Microsoft Entra ID, it is important to carefully consider:
- How users will gain access
- What level of access they should have
Not all users need the same capabilities within an application. For example, some users might need to only view data, others might need to edit content, and a few might require administrative control. Managing these permissions effectively is a key part of both application security and user experience.
A structured way to achieve this is by defining application roles. Application roles represent a formal definition of what actions a user is permitted to perform within an app. By assigning a role to a user (directly, via group membership, or through access packages), you can clearly map responsibilities and ensure that permissions are consistent and predictable.
Some common examples of application roles include:
- Reader / Viewer – can only access and view data or content.
- Contributor / Editor – can create or update content but not manage system-wide settings.
- Administrator – has full access, including the ability to configure the application and manage user access.
- Custom Roles – tailored to specific business needs, such as "Approver," "Project Manager," or "Support Agent."
Benefits of Using Application Roles:
- Clarity: Roles provide a clear description of what a person is allowed to do, reducing ambiguity.
- Consistency: Access can be standardized across multiple applications, making governance easier.
- Scalability: Roles allow you to apply the same access definitions to many users or groups, simplifying large-scale management.
- Security: Enforces the principle of least privilege by granting only the permissions required for the role.
By planning and defining application roles early in the design or integration process, you set a strong foundation for secure, compliant, and user-friendly access management.
Once roles are defined in the app registration, they become available in the Enterprise Application instance that represents the app in your tenant. From there, administrators can assign these roles to users or, more commonly, to Entra ID groups.
Best Practice 14: Review App Registrations on a Regular Schedule
As your organization builds and connects more applications to Microsoft Entra ID, the number of app registrations in your tenant will naturally grow. Over time, some of these apps may become outdated, unused, or misconfigured. If not reviewed and maintained, they can quietly introduce security vulnerabilities and operational risks to your environment.
That is why it is essential to perform regular reviews of app registrations. These reviews help identify apps that are no longer in use, contain stale or expired credentials, or hold permissions that exceed their current purpose. Without this regular housekeeping, your tenant may accumulate orphaned applications—apps that still have active credentials and permissions but no longer serve a business function or are no longer monitored by an owner. These orphaned apps create an unnecessary attack surface, making your environment harder to secure.
A good app review process includes several key checks:
- Credential Validity
Are there any secrets or certificates that are expired or nearing expiration? Old credentials should be removed, and active ones should follow strict security practices, including appropriate lifetimes and secure storage in tools like Azure Key Vault.
- Sign-in Activity
Has the app been used recently? Microsoft Entra ID allows you to check app usage by examining sign-in logs, which are accessible through the Entra Admin Center, or programmatically via the Microsoft Graph API. If an app has not been used in several months and has no clear ownership, it may be a candidate for deprecation or removal.
- Permission Usage
Does the app still require the permissions it has been granted? If an app was initially configured with broad API permissions but now only needs limited access, those permissions should be reduced. This helps maintain the principle of least privilege and limits the blast radius if the app were ever compromised.
- Ownership
Does the app have a clearly assigned owner or sponsor? If no one is responsible for it, there is a high chance that maintenance will be neglected. Apps without owners should either be reassigned or removed from the environment.
Best Practice 15: Use Lifecycle Workflows to Deactivate or Clean Up Apps
When you identify apps that are inactive, unowned, or unnecessary, you can take appropriate action. In many cases, the app can be disabled temporarily by turning off sign-in capabilities via the app’s properties. This allows time to confirm with stakeholders whether the app is still needed or not. If no one claims or reactivates it, the app should be safely deleted to eliminate its credentials and associated permissions. Establishing a recurring review schedule, such as every 3 or 6 months, helps ensure that your app landscape remains clean, secure, and compliant. Reviews should be documented and preferably automated to avoid becoming a time-consuming manual task.
BONUS: Automate App Review with EasyLife 365 Identity
This is where EasyLife 365 Identity provides substantial value. It allows you to automate the review process by:
- Tracking credential expiration
- Monitoring sign-in activity
- Tracking accountability
It also supports lifecycle workflows such as flagging inactive apps, notifying owners, and prompting sponsors for action. With clear ownership data and policy-driven review cycles, EasyLife 365 Identity ensures that no app is forgotten and no security risk is left unmanaged.
BONUS: Conclusion: Keeping Your App Directory Clean, Secure, and Under Control
Managing app registrations in Microsoft Entra ID is a critical responsibility for any organization that relies on Microsoft 365, Azure services, or cloud-based applications. App registrations define how applications identify themselves, authenticate, and gain access to resources. When managed correctly, they provide secure and efficient integration with the Microsoft identity platform. When neglected, they become a source of risk, complexity, and operational headaches.
In this series, we outlined a set of essential best practices to help organizations gain control over their app registrations. We covered the importance of:
- Clearly assigning ownership
- Securing credentials
- Applying the principle of least privilege
- Limiting who can register apps
- Using verified publisher status for external trust
- Defining app roles for structured access control
- Conducting periodic reviews to identify stale or over-permissioned apps
Each of these practices contributes to a more secure, manageable, and compliant identity ecosystem. They are not just technical configurations. They represent operational guardrails that support both IT and business teams in using the Microsoft cloud safely and effectively.
However, implementing and maintaining these practices manually can be challenging, especially as the number of apps in your tenant grows. This is where EasyLife 365 Identity offers powerful advantages:
- Enhances Microsoft Entra ID by introducing dedicated ownership tracking through roles and sponsors
- Manages credential lifecycles with automated alerting
- Enables policy-driven reviews across your entire application landscape
- Brings visibility to app permissions, reducing blind spots
- Simplifies delegation of responsibilities without losing control
- Ensures that every app,regardless of its technical purpose,has a clear path for governance and accountability
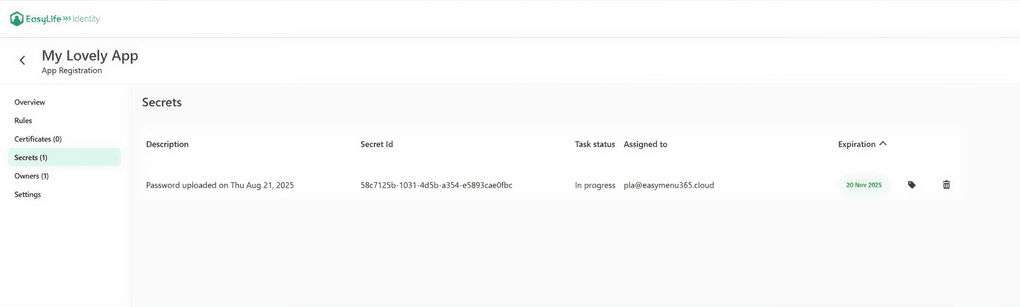
|
|---|
| EasyLife 365 Identity screenshot showing one active app secret for secure credential management. |
By combining Microsoft’s native capabilities with the extended governance features offered by EasyLife 365 Identity, your organization can move beyond reactive management and establish a secure, well-governed foundation for all application integrations. This allows your IT environment to scale safely and sustainably, without losing control over the apps that power your business.
Together with the earlier practices in this series, these final steps help you establish a secure, flexible, and sustainable approach to application identity in Microsoft Entra ID.
Up next: In our next series, we’ll explore how to govern Enterprise Applications, the access points that enforce permissions in day-to-day operations.